ISO 27001:2022 Report on Internal Audit Template
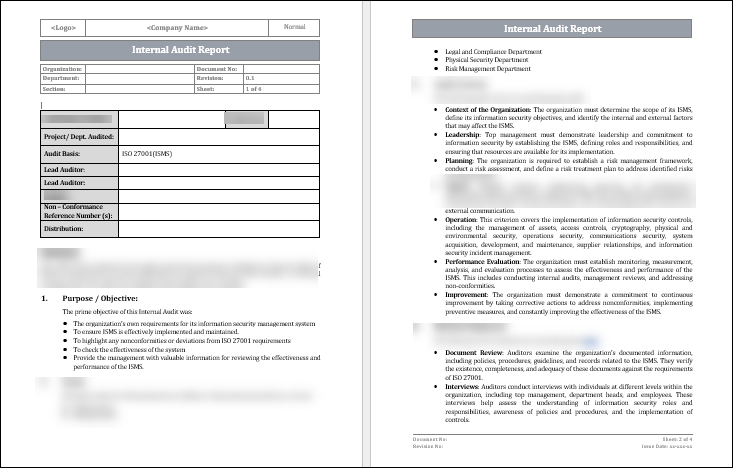
Internal audits are crucial in ensuring ISO 27001 conformity by assessing the organization's controls and practices for information security. These audits evaluate the compliance and effectiveness of the information system management system to the requirements of the standard. The internal audit report is a formal document presenting the audit findings, observations and recommendations. This report will help management gain insight into the information security status of an organization, identify areas that need improvement, and ensure ongoing compliance with ISO 27001.
The Purpose of an Internal Audit Report
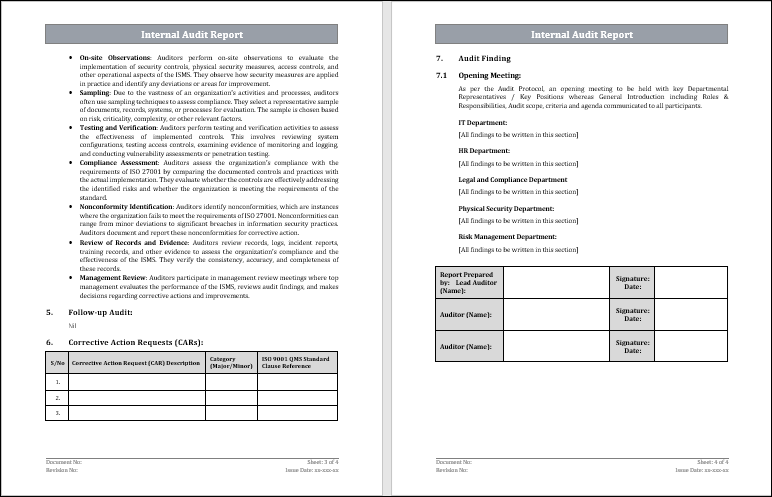
The ISO 27001 internal audit report is intended to be a comprehensive and formal summary of all findings, observations and recommendations that result from the audit process. This report is crucial in ensuring that an organization's Information Security Management System, or ISMS, is effective and achieves ISO 27001 compliance. The internal audit report has three main purposes:
1. Assessment of Compliance: An internal audit report will assess the level of conformity of the organization with ISO 27001. Auditors evaluate the information security practices and controls of the organization against the criteria in the standard to identify areas that are not conforming. This assessment helps management determine the extent to which ISO 27001 is being met by the organization.
2. Identification of Weaknesses & Vulnerabilities: During an internal audit, it is possible to identify weaknesses and vulnerabilities within the organization's controls for information security. They could take the form of outdated security policies, insufficient risk assessments or gaps in security practice. This report allows management to correct these weaknesses and strengthen their ISMS.
3. Continuous Improvement: ISO 27001 stresses the importance of continual improvement for an organization's security practices. The internal audit report gives valuable feedback to the management. This allows them to improve their information security policies and processes. The findings of the audit report can help organizations improve their ISMS and be more responsive to new security threats.
4. Documentation of Best Practices: The audit report does not just focus on the deficiencies, but also recognizes successful implementations. Documenting and recognizing these successful security measures will encourage their replication across the organization. By sharing best practices, an organization can build a stronger culture of security.
5. Communication with Stakeholders: The internal audit reports serve as a transparent, credible communication tool between auditors, management, regulatory agencies, and customers. It shows the organization's commitment towards information security and ISO 27001 compliance, instilling trust in the measures taken for protecting sensitive information.
6. Support Certification and Recertification: The internal audit report provides critical support for ISO 27001 certification and recertification. The internal audit report is a document that shows the organization has conducted internal assessments in order to determine compliance and effectiveness. This helps the certification process go smoothly.
The ISO 27001 internal audit report is a valuable tool to assess compliance, identify weaknesses, promote best practices, support continuous improvement and communicate the organization's dedication to information security. The report's insights and recommendations can help organizations create and maintain an ISMS that is robust and effective, protecting their sensitive data and assets against potential threats.
The Auditing Methods Used
ISO 27001 requires an internal audit to be conducted using a structured and systematic methodology. This is done in order to evaluate an organization's Information Security Management System against the requirements of ISO 27001. Internal audits are crucial to evaluating information security controls and identifying improvement areas. They also ensure compliance with ISO 27001. The following is the methodology that was used to conduct the audit:
1. Audit Planning
- Define Scope: Identify the boundaries of your audit, such as the departments, processes and locations that will be audited.
- Establish Clear Objectives: When planning the audit, set specific objectives, such as assessing the ISMS's effectiveness, identifying any weaknesses and assessing the compliance.
- Choose Auditors: Select auditors who have relevant experience and knowledge in ISO 27001 and information security.
- Create an Audit Plan: Develop a detailed audit plan outlining the audit schedule, audit activities and audit resources.
2. On-Site Assessment
- Interviews: Conduct interviews with key personnel to learn about their roles and responsibilities and how they implement information security controls.
- Evidence Collection: Gather objective evidence by observing, inspecting, and reviewing records to verify implementation and effectiveness.
- Processes: Assess how information security processes are performed, and whether or not they align with ISO 27001.
3. Identify Non-Conformities
- Compare Findings: Compare the ISO 27001 requirements with the evidence collected to identify areas that are non-conforming or deviating from the standard.
- Document Non-conformities: Document any instances of noncompliance with a clear explanation and a reference to ISO 27001 clauses.
4. Prepare Audit Report
- Summary of Findings: In a structured, objective way, summarize the audit's results, including any observations, nonconformities and positive aspects.
- Provide Recommendations: Include recommendations for improvements and corrective actions based on non-conformities identified and best practices.
- Report Distribution: Share your audit report with all relevant stakeholders including the management to facilitate decision making and ensure transparency.
5. Follow-up and Corrective Actions
- Monitor Corrective Action: Track the implementation of corrective measures after the audit to address non-conformities identified.
- Verify Effectiveness: Confirm the corrective action has effectively resolved the identified issues and brought the organization in compliance with ISO 27001.
This methodology allows organizations to conduct internal audits and gain valuable insight into their ISMS practices. They can also take the necessary steps to continually improve their ISMS in order for them ISO 27001 compliance.
Recommendations to Improve
ISO 27001 emphasizes that improvement is a process, which is ongoing and designed to enhance an organization's Information Security Management System. Here are some general suggestions for improvement based on findings from internal audits and risk assessments.
- Regular Risk Assessments: Conducting regular risk assessments will help you identify any new threats, vulnerabilities or risks that may affect your information assets. Update risk treatment plans to reflect the latest security measures.
- Training and Awareness Programmes: Implement comprehensive programs of training and awareness for all employees in order to ensure that they are familiar with information security policies, procedures and best practices. Staff should be educated about the risks they may face and their role in protecting sensitive data.
- Plan of Incident Response: Create and implement an incident response plan that is well defined to handle security incidents or breaches effectively. To ensure the plan's effectiveness, it should be tested through simulations and exercise.
- Vendor Management: Enhance vendor management by assessing security practices and ensuring that third-party vendors adhere to the appropriate security standards. Monitor their performance to ensure compliance.
- Access Controls: Review and improve access controls to critical systems and data. Implement the principle that only those with a need for access should have it.
- Management Security Awareness: Inform senior management of the importance and role they play in supporting security initiatives. Securing management commitment and buy-in to allocate resources to security improvements.
- Security Incidents Reporting: Establish an effective process for promptly reporting security incidents. Encourage an open culture and encourage your employees to share any security concerns they may have without fear of punishment.
- Encryption: Evaluation of the use and effectiveness of encryption, particularly for sensitive data. Encryption protects data, even if unauthorized parties gain access.
- Monitoring and Logging: Use robust monitoring and logging mechanisms to detect suspicious activity and potential security breaches. Review logs regularly and act on anomalies immediately.
- Physical Security: Increase physical security measures in data centers, server areas, and other critical areas that store or process sensitive information.
Conclusion
Internal audit reports serve many purposes. The report provides a comprehensive evaluation of the organization's security practices, controls and processes. It helps identify non-conformance, weaknesses and vulnerabilities. These findings will help management make informed decisions about how to improve their information security continuously.

