ISO 27001:2022 Information Security Management System (ISMS)
The International Standardization (ISO) defines info Security Management System (ISMS) as “a systematic approach to characteristic, dominant, reducing or eliminating risks associated with the confidentiality, integrity, and convenience of information.” In other words, it’s how organizations will effectively manage their info assets from risk management through interference techniques like system hardening.
A good info Security Management System (ISMS) is the core of any info security program. Associate in nursing ISMS aims to shield a company’s info assets from unauthorized speech acts, modification, or loss. These systems are designed to assist organizations in bringing home the bacon compliance with applicable laws and laws for privacy protection. It gives managers all told areas inside an organization with specific actions to handle risks in their structure knowledge. In short, firms use them as a part of their risk management practices by managing vulnerabilities and threats – whether internal or external – that would place business operations in danger if left unaddressed.
An Effective ISMS Should Have Clear Objectives That Identify Measures Taken Toward Achieving These Goals
A System for Managing Knowledge Security
An info Security Management System (ISMS) could be a system for managing knowledge security. The ISMS generally includes procedures, standards, and pointers designed to shield the confidentiality of knowledge assets. It also guides a way to manage potential threats to knowledge and handle incidents if they occur.
To effectively implement associate in nursing ISMS, it’s necessary that your organization trains employees concerning their responsibilities in relevance to the system and supply them with applicable resources.
Not All Knowledge is Treated Equally by the ISMS
The ISMS could be designed to make the info more accessible and easily used. This permits for higher communication between staff, clients, and managers. It will do this by characteristic all sensitive knowledge and storing it in an exceedingly secure location with restricted access. However, not all knowledge is treated equally by the ISMS. These exceptions embrace MasterCard numbers, money info, medical records, in-person place-able info (PII), etc.
Developing an ISMS is Dynamic, Not Static
An ISMS isn’t a static system. It should be dynamic and versatile to react to dynamic business wants internal and external changes within the marketplace. To remain competitive, businesses ought to often review their ISMS to assist them in determining areas for improvement and potential risks.
An Effective ISMS Is Risk-based
Risk Management is the method of characteristic, analyzing, and mitigating threats so they do not negatively impact your company’s business objectives. To be effective during this method, you would like to understand what risks are being sweet-faced by your organization and wherever they originate.
There are many alternative forms of risk: operational risk, cyber security risk, money risk, legal/compliance risk, etc. However, one factor remains constant – while you do not understand all the risks in situ at any given time or location in your company’s business, you may not be ready to mitigate those risks effectively.
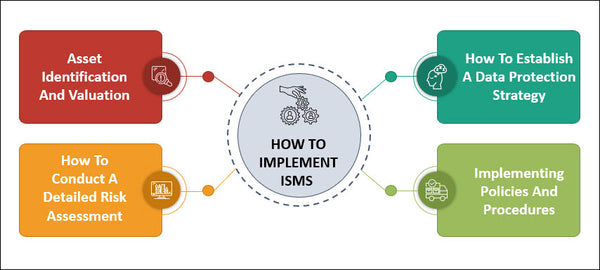
How to Implement ISMS in Your Organization?
An Information Security Management System (ISMS) is a process that identifies the organization’s risks and then plans how to protect it from any security breaches. The ISMS plan should include who is responsible for what, when they do it, and where the assets are located.
Step One: Asset Identification and Valuation
“Asset Identification and Valuation: Step One” is the first step in creating a comprehensive asset inventory. It includes identifying what you own, determining how much it is worth, and prioritizing or categorizing your assets. This will let you know whether the cost of insuring specific items should be increased if they are more valuable than others.
Step Two: How to Conduct a Detailed Risk Assessment
Risk assessment is important for any business. A risk assessment can help you identify your stakes and mitigate the risks that they might face. The first step in conducting a detailed risk assessment is determining what you have at stake if something happens. This includes your physical assets as well as intangible benefits or losses. After you have identified your stakes, it’s time to look for vulnerabilities that could cause damage or loss of these things.
Step Three: How to Establish a Data Protection Strategy
The third step in establishing the ISMS is implementing a monitoring and measuring security system. One of the most important parts of this step is creating an information classification policy that will help determine what information needs to be protected under your ISMS. This can include data on customer or employee personal information, intellectual property, financial statements, etc.
The next step is implementing policies and procedures designed to protect these sensitive pieces of data from unauthorized access or disclosure. These policies should also address how employees store their passwords (e.g., they should not write them down on paper), which computers are authorized for use by certain people (i.e., outside contractors may only have access to specific servers), and how often someone.
Why Organizations Need to Protect Their Data?
Data security is important for many reasons. The three main reasons are confidentiality, integrity, and availability. Confidentiality ensures that only people who are authorized to view a document or dataset have access to it; Integrity ensures that once a document has been created or updated, nobody can change it without leaving a trace; Availability means ensuring that people always have access to any information they may need, regardless of where they are in the world.
Why is Managing Data Security Important?
ISMS may be a framework that will assist you in managing information security at scale. It helps to ensure the protection of all your data, regardless of how it’s kept or how WHO is accessing it. From personal health care records to company monetary records, ISMS has been tested to be a good thanks to keep sensitive information safe.
The Valuable Price of Knowledge Breaches
Data breaches are getting a lot of standards, with the typical price of a knowledge breach costing $3.79 million per incident. However, the Ponemon Institute’s 2018 price of knowledge Breach Study found that this is often up from $3.55 million in 2017 and $3.37 million in 2016. The study also found that the rise may be attributed to increased attack sophistication, size, and length of breaches, still because of the increase in ransomware attacks on attention organizations.”
ISO 27001: Gained Certification by Organizations:
ISO 27001 is a world custom for data security management. It specifies a collection of necessities that must be met to shield data confidentiality, integrity, and availability among a given organization. The certification method begins with a self-assessment section followed by an associate on-the-spot visit from one or many auditors WHO can assess the extent to which the organization has complied with ISO 27001’s necessities.
Four Advantages of Associate ISMS
- A technique for managing data security risks and vulnerabilities associated with threats to an organization’s operations, assets, or services.
- Increased productivity because workers will concentrate on their work while not being a distraction.
- Decreased lost revenue because of information integrity, confidentiality, and availableness breaches.
- Improve client satisfaction through higher service delivery.



