GDPR Request for Confirmation of Authority Template
Introduction
One of the central guidelines of the GDPR is that any data subject (end-user) can request access to their personal data, which is collected and stored on the organization's servers. Most data subjects request access to their data, but it is possible to submit the request on behalf of another end user. The guardian of a minor, a debilitated person, etc, can submit this request. The request should then be catalogued as a third-party one, and the requester is acting as a proxy on behalf of the end-user. It is important to note that such a proxy request cannot be submitted on behalf of a deceased person.
Since the personal data is classified as sensitive, each proxy request must be accompanied by legal proof that the requester is acting as the end-user's legal guardian and has provided sufficient proof of their identity. If the organization shares one of its end-users personal data without proper validation of guardianship, this will be classified as a data breach.
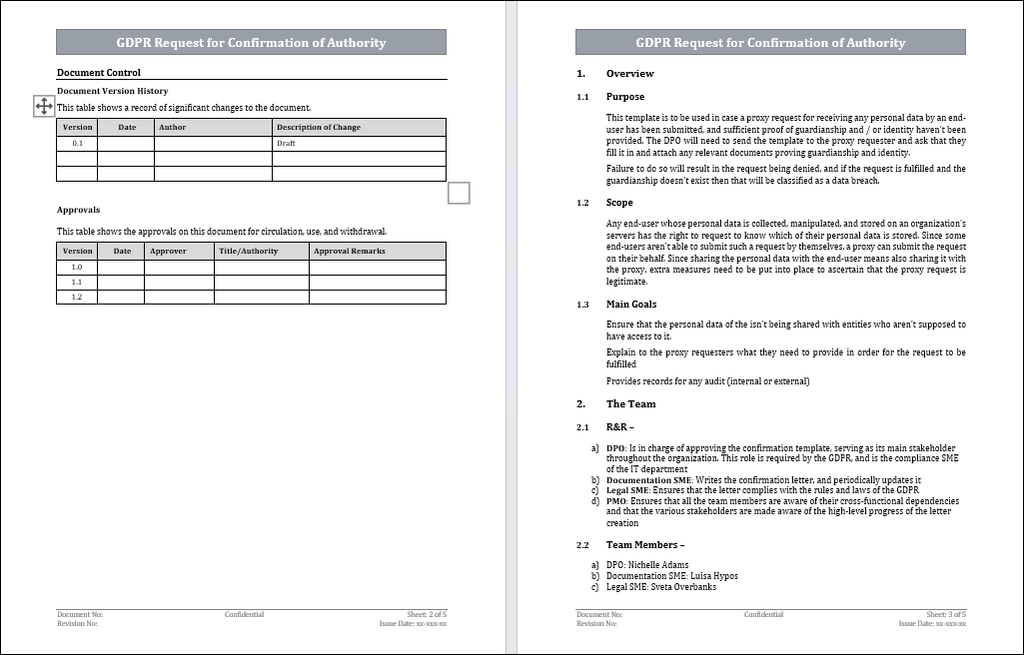
The confirmation of authority is to be used when a proxy request for receiving any personal data by a data subject has been submitted and sufficient proof of guardianship and identity hasn't been provided. The DPO will need to send the confirmation of authority to the proxy requester and ask that they fill it in and attach any relevant documents proving guardianship and identity. Failure to do so will result in the request being denied, and if the request is fulfilled and the guardianship doesn't exist, that will be classified as a data breach.
Scope and Purpose
Any data subject whose personal data is collected, manipulated, and stored on an organization's servers has the right to request to know which of their personal data is stored. Since some data subjects can't submit such a request alone, a proxy can submit it. Since sharing personal data with the data subject means also sharing it with the proxy, extra measures need to be put into place to ascertain that the proxy request is legitimate.
The requester should provide the following documentation for each proxy request-
1. Proof of identification of the requester who is acting as a proxy.
2. Adequate proof of legal authority that the proxy is the legal guardian of the end-user (this is the request for confirmation of authority).
3. The request of the end-user.
4. The end-user credentials: Who is requesting the personal data.
Required Fields in the Request
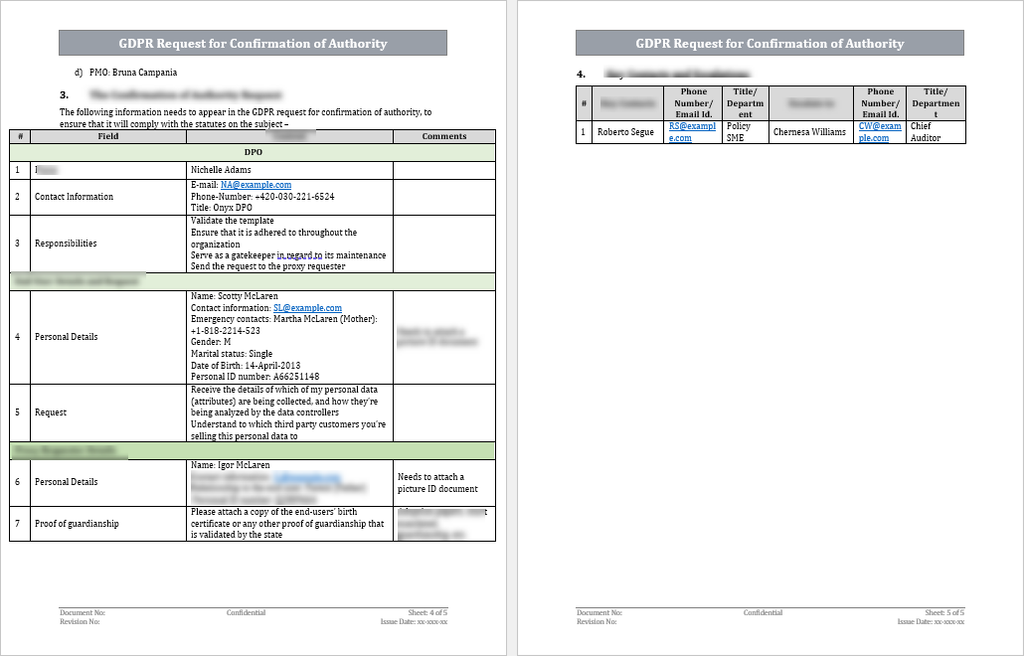
The confirmation should include the following fields -
1. The details of the DPO who signs off on the confirmation.
2. The details of the end user who the proxy is submitting the request on behalf of.
3. The details of the proxy.
4. Which data the request is targeting.
5. Proof of legal authority between the end-user and the proxy.
The Obligations of the Data Controller
1. Ensure that the personal data of the data subject isn't being shared with entities who aren't supposed to have access to it.
2. Explain to the proxy requesters what they need to provide for the request to be fulfilled.
3. Provides records for any audit (internal or external).
4. Validate the template.
5. Ensure that it is adhered to throughout the organization.
6. Serve as a gatekeeper regarding its maintenance.
7. Send the request to the proxy requester.
Term Definitions
What is a Data Controller?
An organization or person who determines the use of the collected personal data from the data subjects. The data controller owns the collected personal data, decides how it will be processed and bears the sole responsibility for safekeeping it.
What is personal data?
Any unique data which relates to an individual data subject. This can include such information as: Name, phone number, Email address, ID number, health records, political opinions, IP address, etc.
What is the processing of personal data?
Any act performed on the collected personal data of all the organizations' data subjects. This may include such actions as storing the data, analyzing it to extract insights or deleting it once it is no longer required.
What is a data subject (also known as an end-user)?
Any person who created a unique username on the organization's website, thus giving them the possibility of using that username to perform specific tasks and use features offered on the website.
Who is the DPO?
The Data Protection Officer is the main stakeholder of the organization for all aspects of GDPR compliance. They are responsible for making sure that the GDPR guidelines are adhered to.
What is a data breach?
Any intentional or unintentional security incident, which involves the sharing of personal data with any unauthorized element. Sharing personal data may include viewing, copying, stealing, or altering personal data.
Key Takeaways / Conclusions
1. The DPO (or their delegate) is responsible for checking the proxy request, and responding to it.
2. In case of a rejection: the response must explain in clear, everyday language why the rejection decision was made.

